If you are looking to Virtualise within Windows 7 look no further than Virtual PC, this brings some of the goodness from Hyper-V to the desktop and as with it’s bigger brother requires Intel VT or AMD-V CPU instructions to be enabled in your BIOS (if you don’t have this and you need to Virtualise then buy a better machine or go and use VMware)
Windows Virtual PC for Windows 7 is available now as a release candidate, but as with the previous Hyper-V beta it is very stable and feature complete (Hyper-V beta was actually shipped with Windows Server 2008 RTM don’t you know?). However, this product alone will not give you the Virtual application publishing required to sandbox a browser, for this you need “XP Mode”, also available in release candidate form.
Before I explain how to blend these two products I want you to understand the benefits of isolating your web browser AKA “sandbox”. When you sandbox a computer application it provides a layer of isolation and therefore a security mechanism for separating running programs. It is often used to execute untested code, or untrusted programs from unverified third-parties, suppliers and untrusted users. The sandbox typically provides a tightly-controlled set of resources for guest programs to run in, such as scratch space on disk and memory. Network access, the ability to inspect the host system or read from input devices are usually disallowed or heavily restricted. Another good example of when “to click or not to click” is whilst browsing links that have been put through URL shortening services such as “bit.ly“, this has become increasingly more popular on Twitter – (Tweets are restricted to 140 characters).
Now how do you do it?
First you need to enable Virtualisation in your BIOS (read here for more information), then install Virtual PC, finally install XP Mode from here.
Once the installation is completed you need to look at Virtual application publishing, a “Virtual application” is an application installed within a VM that can run in a seamless way as if the application were installed on the host computer’s operating system. The user would not necessarily be aware of the existence of underlying VM on which the application is running.
To publish Internet Explorer 6.0 (or any other XP mode application):
- On the virtual machine desktop, open the command prompt.
- On the command prompt, execute: Copy “%USERPROFILE%\Start Menu\Programs\Internet Explorer.lnk” “%ALLUSERSPROFILE%\Start Menu\Programs”
- One (1) file should get copied.
- Wait for a few seconds and verify that IE6 is now published on the host (Windows 7) computer.
- Log‐off and close the virtual machine window.
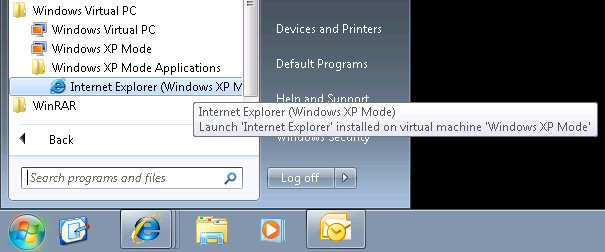
- You can now use IE6 from your Windows 7 start menu.
Windows Virtual PC publishes only applications that are installed in the All‐User profile and Internet Explorer 6 (“IE6”) is installed in a per‐user profile, therefore as detailed in the steps above you are required to copy the shortcut to the “all users” start menu.
Once completed “presto”, you should find a shortcut automatically created in your Windows 7 start menu (full location illustrated below) – this shortcut can then be copied to your desktop or even pinned to your taskbar.