Microsoft’s Teams device strategy leverages Android as a
platform, this currently includes IP Phones and will also incorporate a new
category of devices recently announced at Ignite – Collaboration Bars for
Microsoft Teams, more on this here.
One common occurrence is that when these devices are
connected to Azure Active Directory, Mobile Device Management (MDM) policies
can cause various provisioning errors due to lack of compliance.
Whilst these devices are running Android, they should not be
considered as smartphones, they each run hardened versions of Android that are
closely coupled with SoC-specific drivers. As such they need to be treated
differently, whilst Microsoft publicly
announced deprecation of mainstream support for Android 4.x within Intune, Intune
will continue to support any Teams Android-based devices.
To that end as an admin we need to have a way of excluding Teams devices from MDM policies. To handle this Microsoft recently introduced a new Dynamic Device group within Azure Directory. In this short guide we will create a group, define membership rules and then exclude this group from an existing MDM compliance policy.
First we need to access the Azure Active Directory group
administration portal, here.
We need to ensure we have the appropriate admin permissions for perform this
task.
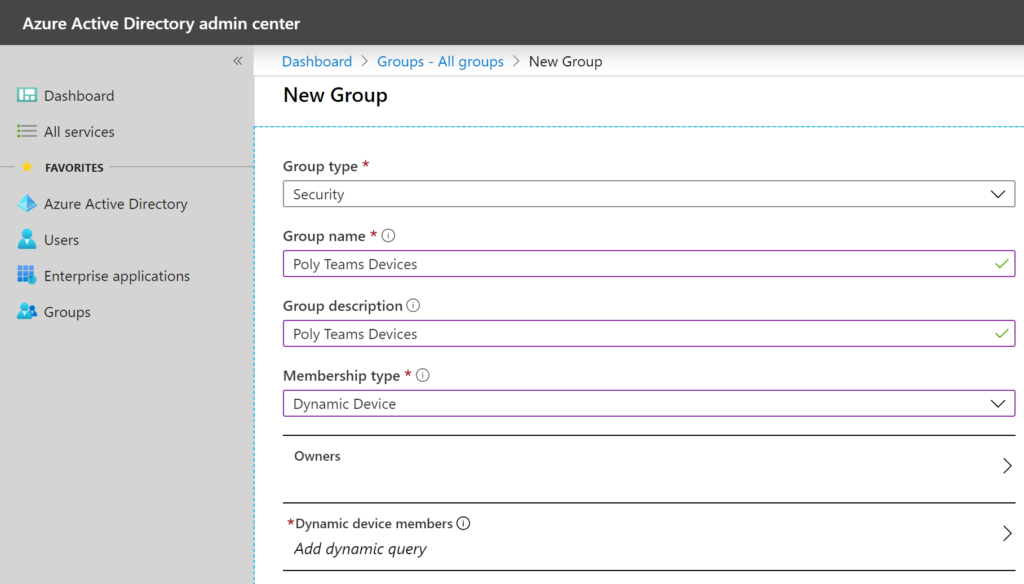
The first thing we’ll do here is create a new group, as per the example below I’ve set the group type to Security and given a friendly name/description. We then need to set our membership type to Dynamic Device.
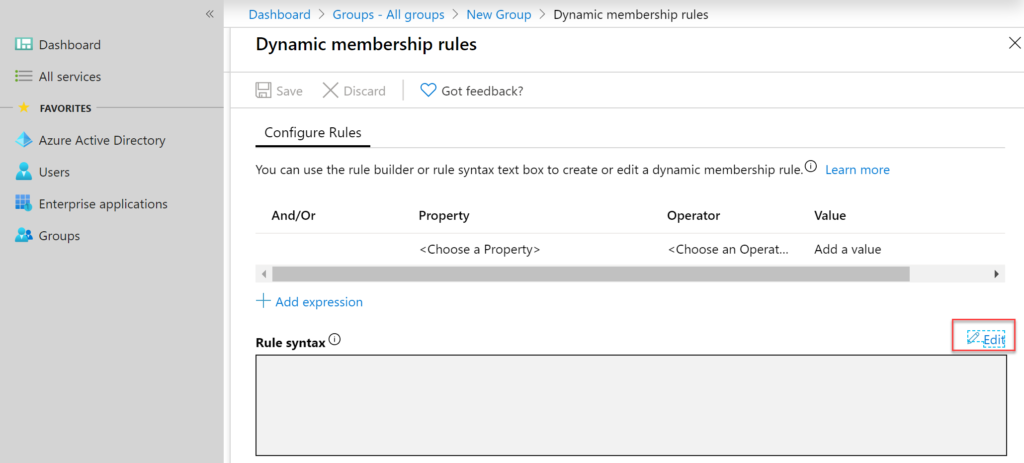
Next, we need to add
a dynamic device query, this will ensure that any new devices are
automatically added to this group upon enrollment.
Once the add dynamic query dialogue is clicked the user interface below is presented. In this example we’re going to manually define a Rule syntax by clicking edit.
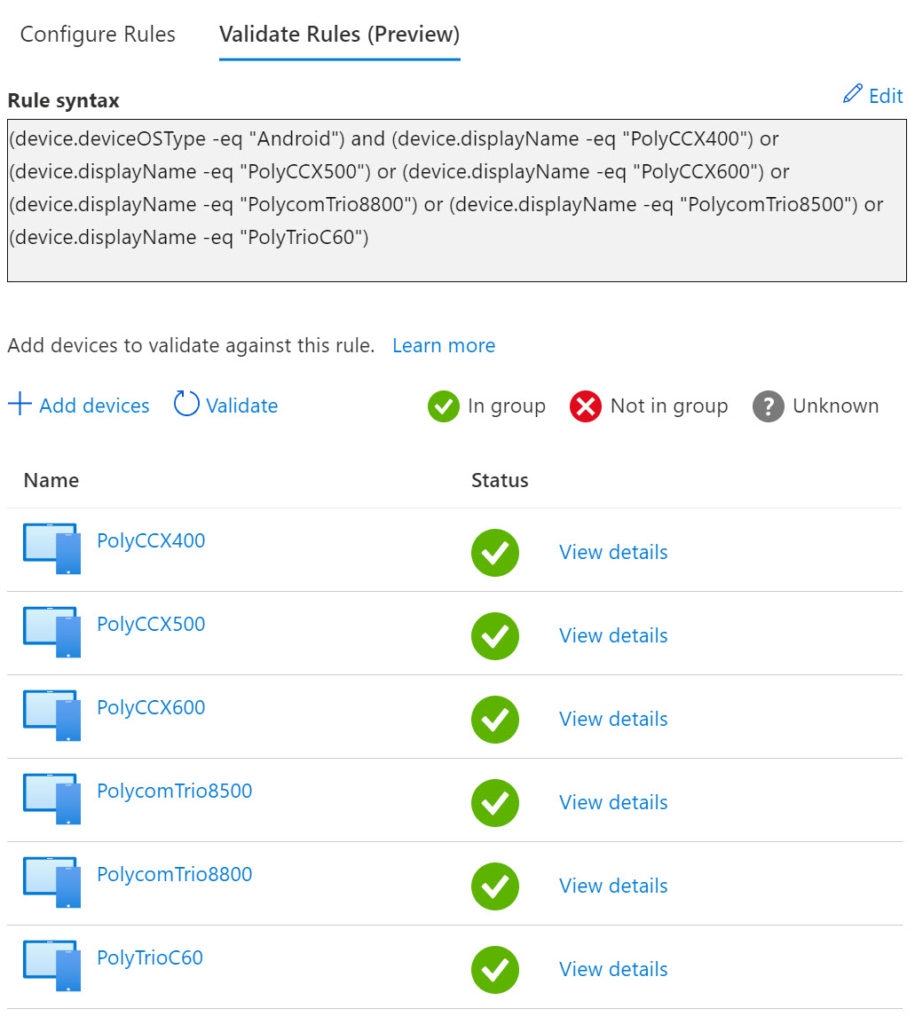
Now we can add our Rule syntax, in this example we’re setting all devices with the OS type Android, with model names of CCX400, CCX500, CCX600, Trio 8500, Trio 8800, Trio C60, Studio X30 and Studio X50
Rule syntax:
(device.deviceOSType -eq “Android”) and (device.deviceModel -eq “CCX400”) or (device.deviceModel -eq “CCX500”) or (device.deviceModel -eq “CCX600”) or (device.deviceModel -eq “Trio8800”) or (device.deviceModel -eq “Trio8500”) or (device.deviceModel -eq “PolyTrioC60”) or (device.deviceModel -eq “PolyStudioX30”) or (device.deviceModel -eq “PolyStudioX50”)
This syntax has recently been updated, instead of referencing the device.deviceModel property we now use device.displayName. Therefore the syntax should now be:
(device.deviceOSType -eq “Android”) and (device.deviceModel -eq “CCX400”) or (device.deviceModel -eq “CCX500”) or (device.deviceModel -eq “CCX600”) or (device.deviceModel -eq “Trio8800”) or (device.deviceModel -eq “Trio8500”) or (device.deviceModel -eq “TrioC60”) or (device.deviceModel -eq “PolyStudioX30”) or (device.deviceModel -eq “PolyStudioX50”)
This can also now be validated as per below:
We can then click, OK
which dismissed this dialogue and then click Save. This returns us to the initial new group creation screen
where we can complete the group setup by clicking Create.
We can validate the group creation by looking at the members
populated automatically by this rule.
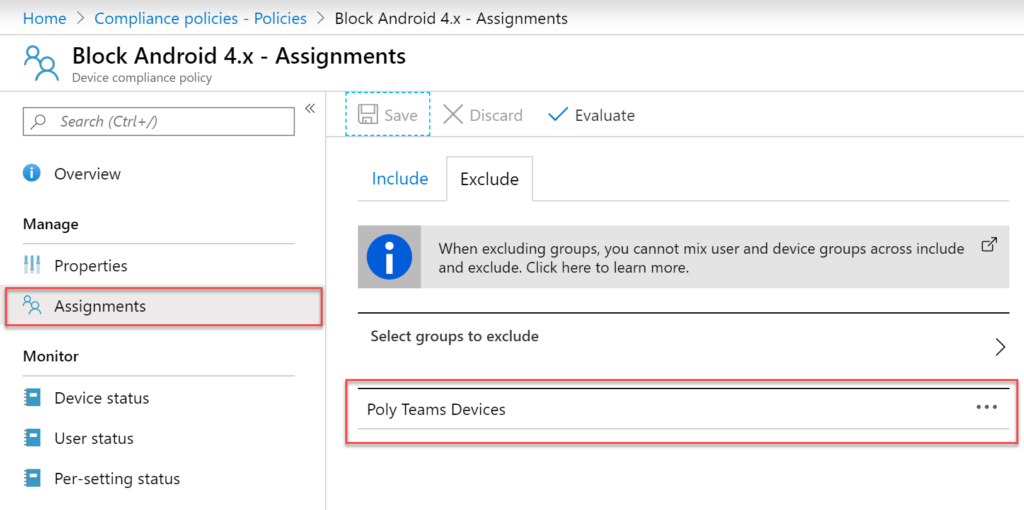
Next, we need to access our existing MDM compliance policy and exclude this group. MDM compliance policies can be edited via Microsoft portal here.
In this example we have a simple compliance policy that is configured to block any devices that are running older versions of Android, specifically 4.x or lower. If we configure the policy Assignments, we can now go ahead and add our group created previously and Exclude this so to ensure our Poly devices are no longer impacted by this check.
I hope this was of help, feel free to comment below and if
you would like to see this demonstrated live please view my presentation from
Ignite here.